www.Irongeek.com: Irongeek's Zaurus Security Tools Page

Zaurus Security Tools
 Hi all, my name is Adrian Crenshaw. I have a strong interest in the topic of
computer security and love futzing around with technology. Most of the best network
security and penetration testing tools are made for *nix environments, so when I heard about the Sharp Zaurus PDA that ran Linux out of the box it tweaked my interest.
The Zaurus makes for a great hacking tool, the price on the older 5500 keeps
dropping (I got mine with a WiFi card and a modem for about $200 off Ebay). The following
are some of the security tools I have running on my Zaurus 5500, the hoops I had to jump
through to install them, and some information on how to use them. While my
testing environment is a Zaurus 5500 running OpenZaurus a lot of this information
should also apply to other Zaurus models and to Ipaqs and Axims running some
kind of ARM Linux. I had a devil of a time installing some of these apps so I
hope this website of my notes helps. If you just want a PDA I would urge you to buy a
Pocket PC or a Palm, but if you like Linux and Networking definitely go for A Zaurus.
If any of the information on this page becomes out of date please email me so I
can update it.
Hi all, my name is Adrian Crenshaw. I have a strong interest in the topic of
computer security and love futzing around with technology. Most of the best network
security and penetration testing tools are made for *nix environments, so when I heard about the Sharp Zaurus PDA that ran Linux out of the box it tweaked my interest.
The Zaurus makes for a great hacking tool, the price on the older 5500 keeps
dropping (I got mine with a WiFi card and a modem for about $200 off Ebay). The following
are some of the security tools I have running on my Zaurus 5500, the hoops I had to jump
through to install them, and some information on how to use them. While my
testing environment is a Zaurus 5500 running OpenZaurus a lot of this information
should also apply to other Zaurus models and to Ipaqs and Axims running some
kind of ARM Linux. I had a devil of a time installing some of these apps so I
hope this website of my notes helps. If you just want a PDA I would urge you to buy a
Pocket PC or a Palm, but if you like Linux and Networking definitely go for A Zaurus.
If any of the information on this page becomes out of date please email me so I
can update it.
Updates: I'm working on updating these
pages to work with OpenZaurus 3.5.1 so bear with me. If a section is marked
with Updated for OZ 3.5.1 Then I have gotten around to checking to
make sure the app and instruction work with version 3.5.1 (Mostly, I do
screw up). Same goes for Updated for OZ 3.5.3. I don't
always have time to keep this site up to date so email me if you have
instructions for newer versions of the software mentioned and I'll update
the site and give you credit.
 |
OpenZaurus
Updated for OZ 3.5.1
Website: http://www.openzaurus.org
Packages:
http://www.openzaurus.org/official/unstable/3.5.1/
Upgrades like OpenSSH:
http://www.openzaurus.org/official/unstable/3.5.1/upgrades/
Install Guide:
http://openembedded.org/oe_wiki/index.php/OpenZaurusInstallGuide
The OpenZaurus ROM gives you more
options than the Sharp ROM, and it's said that OZ has better hardware
support. It's fairly easy to install, just copy the root file system
(opie-image in my case, renamed to initrd.bin) and kernel (zImage) you
want to a CF card and hit the hard reset button while holding down C
and D on the keyboard (if you have big paws it can be tough). See the
install Guide linked above for more details.
Package Management:
You can add packages by put them on
an SD/CF card and using the Package Manager app or the ipkg and
ipkg-link command line tools. The GUI Package Manager seems to be
largely fubared as far as finding packages on CF cards goes, so I
recommend using the command line tools. The basic syntax is as follows
(after you change to the directory the package is in):
To install to ram:
ipkg -d
ram install Whatever-Package3.3_60.ipk
To symlink it into the root file system:
ipkg-link
add Whatever-Package-shortname
If you don't know the short name of a package run the
following command and look though your options:
ipkg list
If you get tired of seeing portmap error use the following
command to get rif of portmap:
ipkg
remove portmap
In OZ 3.5.1 Many of the apps on these
pages will need LibPcap to function, but it seems to be installed by
default with OZ 3.5.1. Before you install any of the Packages I have
mirrored please check in the directories (
http://www.openzaurus.org/official/ ) at the OpenZarus site to see
if there are any newer versions available.
One downside to OZ 3.5.1 is that it
was built with a newer version of gcc then a lot of the apps compiled
for the Sharp ROM which means you will need the compatibility libraries
from
http://www.mithis.com/zaurus/ipkgs/. A newer version of the package
for OZ 3.5.1 can be found here:
oz-compat_0.5-r0_arm.ipk. You will know when you have a
compatibility problem when you get an error like "undefined
symbol: _7QString.shared_null". The GUI tool  that comes with the compatibility libraries does not
always seem to work so what I do is edit the .desktop files and add
"runcompat" in front of whatever the exec= line points to (see my
example in the Zethereal section). Update 3/15/2004: Tim
Ansell (aka Mithro) of the OZ-compat project sent me the following
notes that might help you with GCC compatibility problems: that comes with the compatibility libraries does not
always seem to work so what I do is edit the .desktop files and add
"runcompat" in front of whatever the exec= line points to (see my
example in the Zethereal section). Update 3/15/2004: Tim
Ansell (aka Mithro) of the OZ-compat project sent me the following
notes that might help you with GCC compatibility problems:
| Hi!
I was reading your oz-compat pages (as I
like to look at how people are using my packages) and found the
following information:
"The GUI tool that comes with the
compatibility libraries does not always seem to work so what I do is
edit the .desktop files and add "runcompat"
in front of whatever the exec= line
points to (see my example in the Zethereal section). "
There is actually a better way to do
this, if you go to the console and do a "makecompat <binary>" it
will link up that binary to the compat libs.
I would also like to know more
information on where that script fails so I can fix it :)
I really need to do a quick C++
application instead of being horrible dependent on the old and
unmaintained opie-sh. (I plan to eventually rework and replace opie-sh
with a better opie-sh :)
Anyway I thought i would just inform you
of this :)
Thanks
Tim aka Mithro
|
Some general tips:
1. Make sure you have a good text editor like
Nano installed so you can edit system files, the text editor from
the GUI is flaky as hell.
2. The first thing you you should do after installing OZ is
give the root account a password using the passwd command.
3. Fn-C acts as Ctrl-C would on the desktop.
4. Make sure you have a good SSH and SFTP program on you box.
In Windows I use Putty
for SSH and FileZilla
for SFTPing files. I use EditPad Lite
for editing system files on my Windows box, it does not screw up Unix
style line feeds. Also, upgrade to OpenSSH instead of Dropbear on your
Zaurus so you can do SFTP.
5. Keep the backlight low to extend battery life and have
suspend mode only turn of the LCD when you are wardriving.
6. Space is limited, get yourself an SD card to log
information to.
7. My old instructions say to install LibPcap, almost all of
these apps will need it, but with OZ 3.5.1 it seems to be installed by
default.
|
| |
Change your MAC
Address
Here is how to change you MAC address in OpenZaurus. Iuse
these two commands:
ifconfig wlan0 down hw ether
0:0a:0a:a0:a0:a0
ifconfig wlan0 up
This would set you wlan0 interface to use the MAC
0:0a:0a:a0:a0:a0. This could be useful for sniffing other connections
or for bypassing MAC address restrictions on an Access Point (find
valid MAC addresses by sniffing them). It also makes it less traceable
to your hardware.
|
| |
|
Wardrive Apps
Up and Running:

Config:
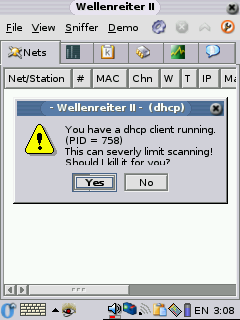
DHCP Warning:
|
Wellenreiter II
Updated for OZ 3.5.3
Website:
http://www.vanille.de/projects/wellenreiter.html
Packages:
http://www.openzaurus.org/official/unstable/3.5.3/upgrades/
This is an ass kicking application that is
still in active development by Michael Lauer (Who seems to have taken
over OZ development). I would recommend checking at his site regularly
to see if there are any updated packages. Wellenreiter II is a great
tool for wardiving, and it not only shows you the APs but also what
other devices are attaching to those APs. You can also get a dump of
some of the traffic that is being passed. With OZ 3.5.3 it's even
easier to install then on the old OZ. The default install of OZ 3.5.3
has all the dependencies already installed, you just need the following
package:
opie-wellenreiter_1.2.0-r1_arm.ipk
Make sure you get 1.2.0-r1 and not
1.2.0-r0 as r0 seems to have issues with some of the other WiFi
software on the ROM (some sort of version conflict between We V16 and
We V17). To install just change to the directory the package is in and
use the two following commands:
ipkg -d
ram install opie-wellenreiter_1.2.0-r1_arm.ipk
ipkg-link add opie-wellenreiter
You may have to restart your Zaurus
after the install to get the icons to appear. When you first run it
give Wellenreiter II a few seconds so it will pop up the message
about killing the DHCP client, once DHCP is killed it works a lot
better. Make sure you choose the proper card under the config page, in
my case wlan0 (I have a TRENDware TE-CF100, if I choose WiFi0 there are
no errors, but no WAPs are ever found either). Wellenreiter II can
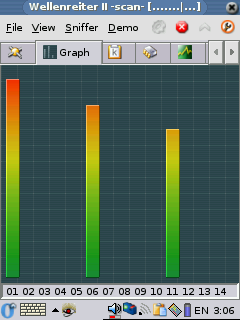
tell you what WAPs it finds, some of the clients, the signal strength
and information about the packets it sees. Wellenreiter II can also
generate a capture dump file that you can later open up in Ethereal on
your pc and see much of the traffic on multiple Waps and SSIDs. It's a
pretty kick ass tool.
Signal Strength:
 |
Packet:
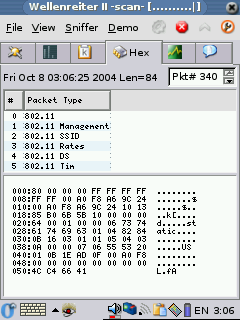 |
|
 |
Kismet
Updated for OZ 3.5.3
Website: http://www.kismetwireless.net/
Packages:
http://www.kismetwireless.net/code/
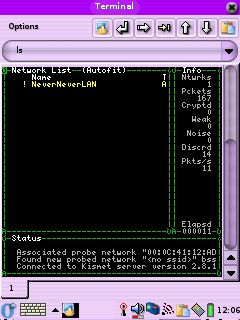
Kismet, you know it, you love it. Kismet is one of the most popular
wardiving tools for Linux. It's great because it can do RF monitoring
and pick up APs that are not broadcasting their SSID (aka:cloaked).
2005-06-R1
These instructions should help you get Kismet 2005-06-R1
working on your Zaurus. First we need to install Ncurses support to get
rid of errors like "Error opening terminal: xterm." To install ncurses
get ncurses_5.4-r7_arm.ipk and ncurses-terminfo_5.4-r7_arm.ipk
from the OZ 3.5.3 feed and libstdc++6_4.0.1-3_arm.deb from the Debian
packages site (http://packages.debian.org/unstable/libs/libstdc++6)
, then use these commands to install them:
ipkg -d
ram install ncurses_5.4-r7_arm.ipk
ipkg-link add ncurses
ipkg -d ram install ncurses-terminfo_5.4-r7_arm.ipk
ipkg-link add ncurses-terminfo
ipkg -d
ram install libstdc\+\+6_4.0.1-3_arm.deb
ipkg-link add libstdc++6
Now we can install Kismet, you can get the deb file for
it from the Debian packages site (http://packages.debian.org/unstable/net/kismet)
Use these commands to install it:
ipkg
--force-depends -d ram install kismet_2005.06.R1-1_arm.deb
ipkg-link add kismet
SIDE NOTE: Now we will have to do some file editing.
I'm a lamer so I don't use the vi package that comes already installed,
I use Nano.You can find Nano in the OZ 3.5.3 feed or at my archive.
It's very easy to install:
ipkg -d
ram install nano_1.3.5-r0_arm.ipk
ipkg-link add nano
Once you have installed Kismet edit the old kismet.conf
(/mnt/ram/usr/local/etc/kismet.conf , it could be in a different path
depending on where you installed it) to reflect the proper source
setting, for my
Ambicom WL1100C-CF 802.11b Wi-Fi card I used:
Replace:
source=none,none,addme
With:
source=hostap,wlan0,hostap
While your at it, it may be a good idea to change where
Kismet dumps log files. This could be useful if you want to dump a lot
of packets to a dump file so you can look at them in Ethereal on your
PC later. In my case, I just wrote them to the RAM mount:
Replace:
logtemplate=/var/log/kismet/%n-%d-%i.%l
With:
logtemplate=/mnt/ram/%n-%d-%i.%l
If you have a Prism2 card you may just want to use my conf
file: kismet.conf. Basically all I
did was tell it to use hostap as the source, you may have to make some
changes if you don't use a Prism based card. Look for the "source="
setting, some possible choices might be:
source=prism2,wlan0,prism2source
source=prism2_avs,wlan0,newprism2source
source=orinoco,eth0,orinocosource
Next edit the kismet script (/mnt/ram/packages/usr/bin/kismet
if you installed it to ram) and add the following lines right after
"#!/bin/sh"
export TERMINFO=/usr/share/terminfo
export TERM=linux
Or you can jus copy of my kismet script here. Now all you should have to do is drop
out to Opie Terminal and type:
kismet
You should now see the Kismet interface we all know and love.
After running Kismet you should see log files in /root with names like:
Kismet-*-1.gps
Kismet-*-1.network
Kismet-*-1.csv
Kismet-*-1.xml
Kismet-*-1.dump
These are basically logs of all the APs you have found, but
the dump file is something special. The dump file contains captured
packets from the networks Kismet has detected, it's in TCPDump format
and can be loaded into other tools like TCPDump, Ethereal and Ettercap
to find out more information about what's running on the network the
packets were captured from. Don't forget to delete these files if you
start to run out of space on your Zaurus.
Thanks to Dave Dmytriw and this thread:
http://www.kismetwireless.net/archive.php?mss:5393:200410:jpjgolgbcmecjmfdlona
for helping me to get the latest version of Kismet to work.
Update 6/20/2005: Jake sent me the following info that
may help some of you that are having problems running Kismet:
I followed the instructions and was getting an error
about 90% of the time that says "FATAL: channel get ioctl failed
22:Invalid argument."
This is resolved by ensuring that the interface is DOWN before
attempting to launch Kismet. Additionally, you have to wait 5-10
seconds after inserting the card (I'm using an Ambicom WL1100C on an
SL-5500 with OZ 3.5.1). It seems obvious but to someone inexperienced
with rfmon, it wasn't. It's not very similar to promiscuous mode on
Ethernet devices.
So, to simplify the process, I just added "ifdown wlan0 &&" to
/usr/local/bin/kismet and I make sure I wait a few seconds before
attempting to start it. If it fails the first time, you can usually
just rerun kismet and it will work.
Have you had this problem? It was somewhat perplexing at first because
_sometimes_ Kismet would run fine and it took a couple hours to find
the sequence that got it started reliably.
|
|
| |
|
Sniffers
DSniff
Updated for OZ 3.5.3
Website:
http://www.monkey.org/~dugsong/dsniff/
DSniff is a great little sniffing package from Dug Song. The DSniff
binary itself parses out passwords from the traffic is sees on the
network. Some of the protocols it supports include smtp, pop3, http
basic and can break ssh and ssl by proxying the connection. The package
also comes along with the binaries arpspoof, filesnarf, mailsnarf,
msgsnarf, urlsnarf, and webspy. So far I've only tested the Dsniff
binary with a standard ethernet card, but it seems to work. I
downloaded the Debian ARM packages from
http://packages.debian.org/unstable/net/ but you can copy them from
my mirror if you wish. You will need the download the files and use the
following commands:
1. Install the needed libraries and the Dsniff package and link them
into the root file system, in my case I'm installing from my SD card. I
got my packages from the Debian unstable branch, but you could get them
from the mirror:
ipkg --force-depends -d ram install
libnet1_1.1.2.1-2_arm.deb
ipkg-link add libnet1
ipkg --force-depends -d ram install dsniff_2.4b1-12_arm.deb
Since I was attached to the Internet via Wi-Fi at the time it
automatically got libice6, libsm6 and openssl from the OpenZaurus feed.
Then I had some more linking to do:
ipkg-link add dsniff
ln /usr/lib/libnet.so.1 /usr/lib/libnids.so.1.20
ipkg --force-depends -d ram install libdb4.2_4.2.52-19_arm.deb
ipkg-link add libdb4.2
ipkg --force-depends -d ram install libnids1.20_1.20-3_arm.deb
ipkg-link add libnids1.20
2. Next just start Dsniff, don't forget to specify an interface. On
my Zaurus, to specify the TE-CF100 10/100 Ethernet card I use the
following command when starting DSniff:
dsniff -i eth0
To use my WiFi card I you use the following command:
dsniff -i wlan0
I've had problems seeing traffic on my wireless LAN, e-mail me and
let me know if the apps work for you. Special thanks to Cowboy and Mark
McLaughlin for the help and encouragement in this section.
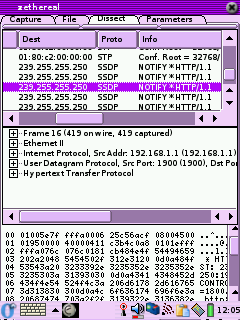 Zethereal
Zethereal
Website:
http://www.cartel-securite.fr/pbiondi/zaurus/zethereal.html
Major Update:1-27-2004
Zethereal is Ethereal for the Zaurus. It's a good little
sniffer/protocol analyzer. All the binaries I've found for it are
compiled with the old gcc so you will have to use the compatibility libraries.
Make sure you have installed LibPcap then install the ipk in my mirror
(provided by Dan L). You will also need to install libglib (my mirror of libglib,
boosted from Debian) and do some symlinking to get it toy work, I
installed it from the SD card as follows:
| |
ipkg -force-depends -d ram install
/mnt/card/libglib1.2_1.2.10-9_arm.ipk
cd /usr/lib/
ln -s /mnt/ram/usr/lib/libglib-1.2.so.0
ln -s /mnt/ram/usr/lib/libglib-1.2.so.0.0.10
ln -s /mnt/ram/usr/lib/libgmodule-1.2.so.0
ln -s /mnt/ram/usr/lib/libgmodule-1.2.so.0.0.10
ln -s /mnt/ram/usr/lib/libgthread-1.2.so.0
ln -s /mnt/ram/usr/lib/libgthread-1.2.so.0.0.10
|
Since this was created with the old gcc you will have to edit the
.desktop file:
nano
/opt/Qtopia/apps/Applications/zethereal.desktop
and change the exec line to read:
Exec=runcompat zethereal-1.0-arm
Restart Opie and it should all work. By the way, if for some reason
installing the IPK does not put icons in the GUI do the following:
ln -s
/mnt/ram/usr/bin/zethereal-1.0-arm /usr/bin/
ln -s /mnt/ram/opt/QtPalmtop/pics/zethereal.png /opt/QtPalmtop/pics/
ln -s /mnt/ram/opt/QtPalmtop/apps/Applications/zethereal.desktop
/opt/QtPalmtop/apps/Applications/
then restart Opie.
Update 6/20/2005: M Delroy sent in the following information
on what he had to do to get Zethereal running on OZ 3.5.3:
Getting Zethereal-1.0-arm Running on OpenZaurus 3.5.3
First install libqt_mt3_3.3.3-r5_arm.ipk
It must be installed into ram.
To do so save the file to the sd card. With OpenZaurus 3.5.3, when
transferred a *ipkg file via syncing from Qtopia 1.7 on Windows the
file is saved to /media/card/Documents/application/ipkg
Issue the following command to install libqt_mt3_3.3.3-r5_arm.ipk in
the directory it is saved in.
ipkg –force-depends –d ram install libqt_mt3_3.3.3-r5_arm.ipk
<enter>
Next create a link with
ipkg-link add libqt_mt3_3.3.3-r5_arm.ipk <enter>
Now install task-opie-minimal_1.0.3_arm.ipk with the following
ipkg -force-depends –d ram install task-opie-minimal_1.0.3_arm.ipk
<enter>
There is no need for a ipkg-link with task-opie-minimal_1.0.3_arm.ipk
Install opie-sh_1.2.0-r0_arm.ipk with
ipkg -force-depends –d ram install opie-sh_1.2.0-r0_arm.ipk
<enter>
Next create a link with
ipkg-link add opie-sh <enter>
We now need to install libpcap0.8_0.8.3-r0_arm.ipk with the following
ipkg -force-depends –d ram install libpcap0.8_0.8.3-r0_arm.ipk
<enter>
No ipkg-link is needed.
Now install libpcap0_0.7.2_arm.ipk with
ipkg -force-depends –d ram install libpcap0_0.7.2_arm.ipk <enter>
This installs the libpcap0_0.7.2 files into /media/ram/packages/usr/lib
However, OpenZaurus needs links located in /usr/lib to the files in
/medial/ram/packages/usr/lib Create the links with the following:
Cd into /media/ram/packages/usr/lib and make sure libpcap0_0.7 files
are located there.
Cd into /usr/lib and issue the following command for each
libpcap0_0.7.2 file
ln -s /media/ram/packages/usr/lib/”libpcap0_0.7.2 file name”
<enter>
Reboot and make sure the links are still in place.
There is no need for ipkg-links with libpcap0_0.7.2
To work around the quickexec not found error when installing
sharp-compat-libs we need to do the following:
Cd into /media/ram/packages/etc/init.d/ and see if quickexec is there.
To create a link to /media/ram/packages/etc/init.d/quickexec in
/etc/init.d issue the following command
ln -s /media/ram/packages/etc/init.d/quickexec /etc/init.d <enter>
Now install sharp-compat-libs_0.5-r2_arm.ipk with the following
ipkg -force-depends –d ram install sharp-compat-libs_0.5-r2_arm.ipk
<enter>
Now cd into /etc/init.d and delete the link to quickexec
Create a link for sharp-compat-libs with the following command
ipkg-link add sharp-compat-libs <enter>
Install libglib_1.2.0_arm.ipk with the following
ipkg -force-depends –d ram install libglib_1.2.0_arm.ipk <enter>
This installs libglib_1.2.0 files to
/media/ram/packages/home/root/usr/lib/ However OpenZaurus needs links
to these files located in /usr/lib
Cd into /media/ram/packages/home/root/usr/lib/ and make sure that there
are libglib_1.2.0 files located there. The following files should be
present.
libglib-1.2.so.0
libglib-1.2.so.0.0.10
libgmodule-1.2.so.0
libgmodule-1.2.so.0.0.10
Create the links by cding into /usr/lib and issue the following for
each libglib_1.2.0:
ln –s /media/ram/packages/home/root/usr/lib/”libglib_1.2.0 file name”
Such as
ln -s /media/ram/packages/usr/lib/libglib-1.2.so.0
ln -s /media/ram/packages/usr/lib/libglib-1.2.so.0.0.10
ln -s /media/ram/packages/usr/lib/libgmodule-1.2.so.0
ln -s /media/ram/packages/usr/lib/libgmodule-1.2.so.0.0.10
We still need libglibthread files so Install
libglib1.2_1.2.10-9_arm.ipk by doing the following
ipkg -force-depends –d ram install libglib1.2_1.2.10-9_arm.ipk
<enter>
This installs libglib1.2_1.2.10-9 files to /media/ram/packages/usr/lib
However OpenZaurus needs links in /usr/lib to the files in the
/media/ram/packages/usr/lib location
Cd into /media/ram/packages/usr/lib and confirm that the following
files are located there:
libgthread-1.2.so.0
libgthread-1.2.so.0.0.10
cd into /usr/lib and create links for the libglibthread files with the
following commands
ln -s /media/ram/packages/usr/lib/libgthread-1.2.so.0
ln -s /media/ram/packages/usr/lib/libgthread-1.2.so.0.0.10
Reboot and make sure the links in /usr/lib are still present.
You can now install zethereal_1.0_arm.ipk with the following command
ipkg -force-depends –d ram install zethereal_1.0_arm.ipk <enter>
Create a link for zethereal with
ipkg-link add zethereal-1.0 <enter>
Reboot and follow the instructions at
http://opie.handhelds.org/cgi-bin/moin.cgi/oz_2dcompat_20HowTo
On how to start Zethereal using the oz-compat (sharp-compat libraries).
Note: Zethereal did not appear to function with new libglibs and
libpcap so use the versions mentioned in this document.
When using zethereal you may find that it starts more reliably via the
zethereal-1.0-arm command rather then the icon.
Zethereal does not place the nic in monitor mode. To place the nic in
monitor mode you may need to first open zethereal via the
zethereal-1.0-arm command. Then without closing zethereal open a second
console session and issue the following command
ifconfig wlan0 down
iwpriv wlan0 monitor 2 x <enter>
where x=the channel you wish to monitor
Check that the nic is truly in by issuing
iwpriv wlan0|more <enter>
You should see monitor mentioned in the output
Bring the nic up with the ifconfig wlan0 up command. Close this console
session and re-enter zethereal.
Under the capture tab make sure that wlan0 is chosen for the nic, enter
a maximum number of packets, and click start.
Note: The packet view under the dissect tab does not update in real
time. When the capture completes or after you click stop re-entering
the dissect tab will show the packets captured. |
|
Ettercap
Website: http://ettercap.sourceforge.net/
I found that you can get the Debian ARM packages to work on
the Zaurus if you just rename them with a .ipk on the end. Make sure
you have installed LibPcap. To install you will have to force
dependences and symlink as follows (your paths may vary, I installed
Ettercap off of an SD card):
ipkg -force-depends -d ram install
/mnt/card/ettercap_0.6.b-2_arm.ipk
ipkg -force-depends -d ram install
/mnt/card/ettercap-common_0.6.b-2_arm.ipk
ln -s /mnt/ram/etc/ettercap/ /etc/ettercap
ln -s /mnt/ram/usr/sbin/ettercap /usr/sbin/ettercap
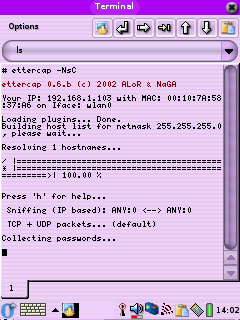
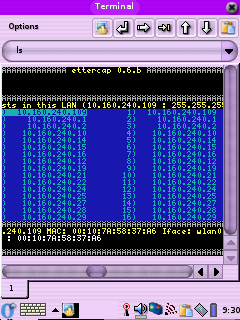
The first pic shows the use of the flags needed to do a
password capture with the IP base sniffing method in command line mode.
To see it in its non command line mode (2nd pic) make sure you turn off
wrapping under the Options menu of Konsole and that the onscreen
keyboard is not up, otherwise you get an error like "Screen must be at
least 25x80 !!". If you get an error about not being able to find
etter.ssl.crt make sure you ran the symlink command above. I'm still
having problem getting it to do IP forwarding, even if I do a:
echo 1 >
/proc/sys/net/ipv4/ip_forward
I'll try to let you know more when I get more time for
testing, it may just be that it does not work with WI-Fi (I have a
10/100 Ethernet card on the way for testing). For the time being when
it arpspoofs the two host it kills all communications between them. If
Ettercap trys to sniff the USB connection (which is most likely not
what you want) make sure you specify what interface to use with the
"-i" option:
ettercap -i wlan0
If Ettercap loads too slowly because of host name resolution
just turn it of using the "-d" option.
Update 2/6/04: Ok, after testing it with a 10/100
Ethernet card Ettercap still does not work for catching passwords, must
be something Zaurus specific because I got the package from Debian and
I'm sure they tested it on other ARM platforms. For right now Ettercap
on the Zaurus is only good for fingerprinting computers and for killing
their net access (packet forwarding does not seem to work). I'll have
to try the Dsniff package to see if I can get it to work better.
|
 |
Ngrep
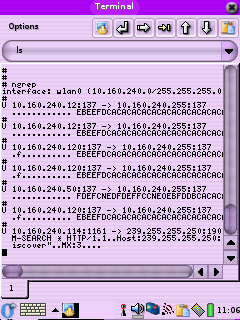
Website: http://ngrep.sourceforge.net/
Ngrep is basically Grep for network packets. It has a lot of
filter options so check out the webpage for all of the options. The
link above is to a binary, copy it to some place like /mnt/ram/usr/bin/
and symlink it to someplace in your path ( ln -s
/mnt/ram/usr/bin/ngrep /bin/ngrep). If you want to save the
information instead of show it on the screen use a command like:
ngrep > /mnt/card/ngrep.log
to pipe it to a file for later viewing.
|
 |
TCPDump
Website: http://www.tcpdump.org/
John H.Sawyer
pointed out that I did not list TCPDump, so here it is. Not a bad
little command line sniffer See all of the options here:
http://www.tcpdump.org/tcpdump_man.html
|
Scanners and PAcket Tools
 Nmap
Nmap
Updated for OZ 3.5.3
Website: http://www.insecure.org/nmap/
The only version on Nmap I have found that
has be directly ported to the Zaurus is 3.27, but you can get the newer
Debian ARM packages (available here:
http://packages.debian.org/unstable/net/nmap ) to function with a
little work. I'll be using version 3.93-1, which I have at my mirror.
Download the following files:
| |
libssl0.9.7_0.9.7e-r1_arm.ipk
libcrypto0.9.7_0.9.7e-r1_arm.ipk
libstdc++5_3.3.6-10_arm.deb
libstdc++6_4.0.2-2_arm.deb
libpcre3_6.3-1_arm.deb
nmap_3.93-1_arm.deb |
 Or you can also download libssl0.9.7_0.9.7e-r1_arm.ipk and libcrypto0.9.7_0.9.7e-r1_arm.ipk from the
OpenZaurus feed at
http://www.openzaurus.org/official/unstable/3.5.3/feed/libs/. You
can get the Debian packages for nmap, libpcre, libstdc++5 and libstdc++6 from
http://packages.debian.org/unstable/ as of the date of this writing.
Or you can also download libssl0.9.7_0.9.7e-r1_arm.ipk and libcrypto0.9.7_0.9.7e-r1_arm.ipk from the
OpenZaurus feed at
http://www.openzaurus.org/official/unstable/3.5.3/feed/libs/. You
can get the Debian packages for nmap, libpcre, libstdc++5 and libstdc++6 from
http://packages.debian.org/unstable/ as of the date of this writing.
Following these step by step instructions
to install Nmap 3.81-2 on your Zaurus. All of them can be performed by
secure shelling into your Zaurus or using the keypad at the Opie
Terminal window:
1. Copy the five files listed above (in red) to a CF or SD card (I
will use the CF card in my examples). Insert the card then change
directories into whatever card you put them on.
cd /mnt/cf/
2. Install libcrypto and link it:
ipkg -d ram
install libcrypto0.9.7_0.9.7e-r1_arm.ipk
ipkg-link add libcrypto0.9.7
Ignore any errors as long as it says "Successfully done" at the end.
3. Install libssl and link it:
ipkg -d ram
install libssl0.9.7_0.9.7e-r1_arm.ipk
ipkg-link add libssl0.9.7
Ignore any errors as long as it says "Successfully done" at the end.
4. Install libstdc++5 and libstdc++6 and link them:
ipkg
--force-depends -d ram install libstdc\+\+5_3.3.6-10_arm.deb
ipkg-link add libstdc\+\+5
ipkg
--force-depends -d ram install libstdc\+\+6_4.0.2-2_arm.deb
ipkg-link add libstdc\+\+6
Ignore any errors as long as it says "Successfully done" at the end.
4.5. If you installed the OZ version of pcre to get
Konqueror to work remove it:
ipkg remove pcre
Otherwise just go to step 5.
5. Install libcre3 and link it:
ipkg --force-depends -d ram install libpcre3_6.3-1_arm.deb
ipkg-link add libpcre3
5.5. If you
installed the OZ version of pcre to get Konqueror to work (or plan to
install it later) symlink libpcre so Konqueror can find it:
ln -s /usr/lib/libpcre.so.3 /usr/lib/libpcre.so.0
ln -s /usr/lib/libpcreposix.so.3 /usr/lib/libpcreposix.so.0
If you install Konqueror later you will have to force depends:
ipkg --force-depends -d ram install konqueror-embedded_20030705-r3_arm.ipk
ipkg-link add konqueror-embedded
Otherwise just go to step 6.
6. Install Nmap 3.93-1 and link it and it's support files:
ipkg -force-depends -d ram install nmap_3.93-1_arm.deb
ipkg-link add nmap
You can find the full man page for Nmap at http://www.insecure.org/nmap/data/nmap_manpage.html
but here are a few useful flags:
-P0 Don't ping first, this is useful because a lot of
hosts turn of ICMP echo requests now.
-O Do an OS detection
-e Specify and interface (eth0, wlan0, etc)
-sV Version scan, find out the version of the
daemon that's listening on an open port.
-A Does the same thing as doing a -O and -sV at
the same time. This switch may do some other things in the future, ask
Fyodor. :)
Also check out my videos:
http://www.irongeek.com/i.php?page=videos/nmap1
http://www.irongeek.com/i.php?page=videos/nmap2
THC-Hydra
Mark Owen sent me the following instructions for getting
THC-Hydra to work on the Zaurus. Thanks Mark:
From: Mark Owen [mailto:mr.markowen@gmail.com]
Sent: Sun 1/16/2005 1:22 PM
To:
openzaurus-users@lists.sourceforge.net
Cc: irongeek@irongeek.com
Subject: THC-HYDRA Zaurus howto
Don't know if this will be of any use to anyone but I have
successfully installed THC's hydra ARM binary release on my 3.5.2 5500
Zaurus.
THC-Hydra is a dictionary attack application that supports
TELNET, FTP, HTTP, HTTPS, HTTP-PROXY, LDAP, SMB, SMBNT, MS-SQL, MYSQL,
REXEC, CVS, SNMP, SMTP-AUTH, SOCKS5, VNC, POP3, IMAP, NNTP, PCNFS,
ICQ, SAP/R3, Cisco auth, Cisco enable, and Cisco AAA
(incorporated in telnet module).
I am going to use it for testing in-house servers and
password vulnerability demonstration to clients. I
recommend it for only LEGAL USE AS USING IT OTHERWISE CAN GET YOU IN
SERIOUS TROUBLE! It required a little sym linking but it works rather
well overall. The program's site is at http://thc.org/thc-hydra/
I've created the following step by step howto on its installation.
It requires libssh, libssl-dev, and libssl to run correctly. This
howto expects you to know how to download and install them.
Just run the following commands to successfully install
it. cd
wget
http://thc.org/thc-hydra/hydra-4.5-arm.tar.gz
gunzip hydra-4.5-arm.tar.gz
tar xvf hydra-4.5-arm.tar
cd hydra-4.5-arm
ipkg install libssh_0.1_arm.ipk #Could
not find in feed but includedin download
ln -s /usr/lib/libssl.so.0.9.7
/usr/lib/libssl.so.0.9.6
ln -s /usr/lib/libcrypto.so.0.9.7
/usr/lib/libcrypto.so.0.9.6
echo /lib/libgcc_s.so.1 >
/etc/ld.so.preload
ipkg install hydra_4.5_arm.ipk
hydra -h
#DONE!
If you have any problems feel free to e-mail me back.
Mark Owen
|
| Nemessis
Updated for OZ 3.5.1
Website: http://nemesis.sourceforge.net
Nemesis is packet injection utility.
It allows you to spoof other hosts and generally cause confusion on the
network. I just took the Debian ARM packages and renamed them with a
.ipk on the end. The package comes with the following utilitys:
nemesis-arp
nemesis-rip
nemesis-dns
nemesis-tcp
nemesis-icmp
nemesis-udp
nemesis-igmp
nemesis-osp
I wanted to get the newest package I could find
(nemesis_1.32+1.4beta3-2_arm.deb) to work but I can't find a version on
Libnet0 that I can install on my Zaurus. I decided to use the older
version, 1.32-5. To install from the CF card do the following commands:
ipkg -force-depends -d ram install
/mnt/cf/nemesis_1.32-5_arm.ipk
then symlink everything someplace in you path:
ln -s /mnt/ram/usr/sbin/n* /bin/
Since the libpcap libray files have a different name in OZ
3.5.1 we have to do the following symlink so nemesis can find it:
ln -s /usr/lib/libpcap.so.0.7
/usr/lib/libpcap.so.0
One cool use is to fake out an IDS system. If I used the
command
nemesis-tcp -x 1025 -y 22 -S
207.46.134.157 -D 192.168.240.7
it would make it look as if Microsoft.com was attacking the
target host. Here is a example of a script I wrote that can be used to
make it look like another host is doing a port scan:
| frame.sh (just copy the content below) |
for port in 21 22 23 25 80 138 139 6776 10008 31337
do
nemesis-tcp -x 1025 -y port -fS -S $1 -D $2
done
|
copy all that into a text file, chmod +x it and use it by
issuing a command like
frame.sh Farmed_ip Target_IP
You will most likely want to change your MAC address first.
|
A note on modems and wardialing from a Zaurus:
Knightmare sent me some notes on wardialing from the Zaurus, and since I had
no better category to post them in I'll put them here:
Hi Irongeek,
The Trendnet Compact Flash 56k V.90 Modem arrived friday. I have
spent most of the day working with it, and managed to wardial a
test PBX we have here. Some notes on my endeavour are:
it was detect out the box on OpenZaurus 3.5.4, OZ popped up with a
dialog box asking to configure it.
I use minicom to wardial, with a war-dialing SALT script from
http://www.textfiles.com/uploads/wardial.txt which is for DOS
Telix,
but is compatible with minicom. You do need to edit the exchange to
scan by hand, but a quick sed/nano 1 line edit is an easy trade off.
This script uses minicom, and is confirmed as working with the UK
phone system, and I would guess other european systems too, which is
quite helpful.
For the actual brute force attacks on mailbox passwords, I used THC
login hacker (login_hacker-1.1.tar.gz) This is also a minicom script,
so cuts down on dependencies, as well as being easy to edit.
A really odd thing I noticed was with the modem's kernel module;
8390.o is missing. I will need to hunt around and perhaps compile a
module for this. Although the device is seen by OZ 3.5.4, and works
for a wardial; dial-up Internet doesn't work due to the missing
8390.o file. I have no idea why this doesn't prevent the modem from
doing a wardial. It's the wierdest thing I have seen on a Linux box
yet!
I found a post stating how a guy made this modem work for dialup
with his 5500, but I cannot seem to find the link again, and my
browser cache at work was cleared. When I find the posting again, I
will forward on an update.
Hopefully this info has been of some use to you. If you do decide to
add it on the site, could I ask you to use my Handle Knightmare, and
not to post my email address...? Thanks.
PS: The 770 is schedules for delivery soon, so I will post a seperate
email with info on that.
|


 Hi all, my name is Adrian Crenshaw. I have a strong interest in the topic of
computer security and love futzing around with technology. Most of the best network
security and penetration testing tools are made for *nix environments, so when I heard about the Sharp Zaurus PDA that ran Linux out of the box it tweaked my interest.
The Zaurus makes for a great hacking tool, the price on the older 5500 keeps
dropping (I got mine with a WiFi card and a modem for about $200 off Ebay). The following
are some of the security tools I have running on my Zaurus 5500, the hoops I had to jump
through to install them, and some information on how to use them. While my
testing environment is a Zaurus 5500 running OpenZaurus a lot of this information
should also apply to other Zaurus models and to Ipaqs and Axims running some
kind of ARM Linux. I had a devil of a time installing some of these apps so I
hope this website of my notes helps. If you just want a PDA I would urge you to buy a
Pocket PC or a Palm, but if you like Linux and Networking definitely go for A Zaurus.
If any of the information on this page becomes out of date please email me so I
can update it.
Hi all, my name is Adrian Crenshaw. I have a strong interest in the topic of
computer security and love futzing around with technology. Most of the best network
security and penetration testing tools are made for *nix environments, so when I heard about the Sharp Zaurus PDA that ran Linux out of the box it tweaked my interest.
The Zaurus makes for a great hacking tool, the price on the older 5500 keeps
dropping (I got mine with a WiFi card and a modem for about $200 off Ebay). The following
are some of the security tools I have running on my Zaurus 5500, the hoops I had to jump
through to install them, and some information on how to use them. While my
testing environment is a Zaurus 5500 running OpenZaurus a lot of this information
should also apply to other Zaurus models and to Ipaqs and Axims running some
kind of ARM Linux. I had a devil of a time installing some of these apps so I
hope this website of my notes helps. If you just want a PDA I would urge you to buy a
Pocket PC or a Palm, but if you like Linux and Networking definitely go for A Zaurus.
If any of the information on this page becomes out of date please email me so I
can update it. 







 Zethereal
Zethereal



 Nmap
Nmap Or you can also download libssl0.9.7_0.9.7e-r1_arm.ipk and libcrypto0.9.7_0.9.7e-r1_arm.ipk from the
OpenZaurus feed at
Or you can also download libssl0.9.7_0.9.7e-r1_arm.ipk and libcrypto0.9.7_0.9.7e-r1_arm.ipk from the
OpenZaurus feed at